Understanding Doxxing Escalation
A Practical Guide
Doxxing and coordinated harassment rarely happen all at once. Most incidents develop in stages, with early signals appearing well before anything becomes visible or disruptive.
Understanding these stages can help individuals and organizations recognize risk sooner, prepare appropriately, and respond in a more coordinated way.
This guide outlines the most common escalation phases and what each one typically looks like.
Not every situation follows this exact path, and many stop before reaching later stages. The purpose of this framework is to make patterns easier to recognize, so you can be prepared.
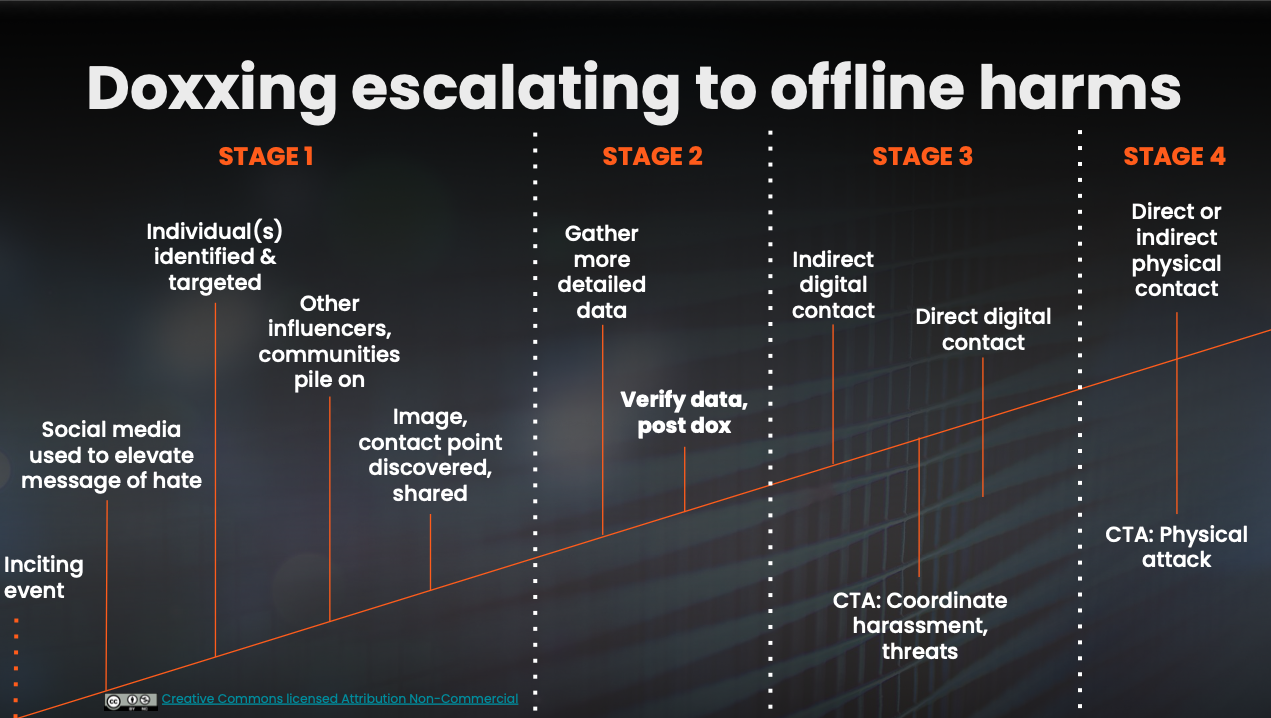
Stage 1: Hating an idea to targeting an individual
A dox often originates with a specific event or trigger, such as:
A broader news cycle that brings attention to an issue or organization
Media coverage of a movement or an organization
An organizational action that draws criticism
A public statement, decision, or announcement made by an organization, signed by individuals
Media coverage of a movement or an organization that highlights an individual
Social media posts by an organization or individual that get noticed and taken out of context
At this stage, discussion may begin with an issue or organization, but quickly becomes personal. People may express disagreement with an issue, and, by extension, the organization.
An early sign of escalation is when attention narrows to a specific individual – a leader, the person quoted in the news piece or social media post, or the communications staff member delivering the messages.
Many of these conversations focus on petty criticisms — a person’s looks, their likes or posts, their family members. Most of this activity remains online, in public fora or private or semi-private forums.
On its own, this activity is not necessarily concerning.
Escalation becomes more likely when the attention continues over time and begins to include indicators such as:
Repeated mention of a specific person’s name
Increasingly personalized blame
Assigning responsibility for broader issues to one individual
We pay close attention to escalation when we see:
others being invited into the discussion, and
posts tagging in additional people or groups.
Not all targeting escalates further. Recognizing this phase early allows organizations to prepare internally — briefing staff, reviewing response plans, and supporting the person involved.
Stage 2: Petty to pointed
If the conversation continues to build momentum, and multiple people and groups begin focusing on one person, risk increases.
At this stage, calls to action are often indirect or exploratory rather than explicit, such as:
“Someone should get this girl’s number.”
“Let’s find out where she lives.”
Information-seeking — asking where someone lives or works — can quickly intensify. Group dynamics often encourage people to dig deeper or share more.
Threads may begin to zero in on identifying details:
“Which John Smith are we looking for?”
“What state does he live in?”
“Looks like he worked here, I think this is his work email address” and
“I found his phone number, I’m pretty sure this is him.”
From there, conversations may move toward explicitly locating a home address, family members, workplaces, or contact details.
Some incidents stall out at this stage if information can’t be verified or found.
Stage 3: Crossing the digital divide
If escalation continues, the next step often involves attempts to connect with the target digitally.
Before any direct contact attempts, the group may try to gain access to the social media or email accounts they presume belong to the targeted person. Notifications from Instagram or Snapchat that someone’s trying to access your account could be an early indication of an escalating situation.
Secure your accounts!
The best case scenario is that attackers try to gain access and fail. To ensure they don’t get access - both to all of the data in your accounts and to post from them and use them as though they’re you, we recommend reviewing this open source, regularly-updated guidance from our colleagues at The New York Times, or using Blockparty to maximize your privacy across social media platforms.
Some other non-direct contact attempts that have serious consequences include:
Posting threats publicly
Creating impersonation accounts
Using AI to generate explicit or defamatory images
Because digital contact carries limited accountability, it’s not a significant leap for attackers to:
Send harassing direct messages or emails
Send threatening texts
This is typically when incidents become visible to the person being targeted.
Stage 4: Showing up IRL
Not every incident reaches this stage. Many of these events stall out when individuals can’t be identified.
When escalation continues offline, it may include:
Unwanted deliveries or mail
Images of the targeted person’s home or workplace sent to them via email or text, indicating that they know where the target lives
Other attempts to intimidate offline
Continued online escalation encouraging contact or in-person action
People showing up at a home or workplace
At this point, coordinated organizational response becomes important — including communications, staff awareness, safety planning, and direct support for affected individuals.
Earlier Visibility + Shared Responsibility
Although incidents often center on one person, they affect the broader organization. Targets are chosen because of what they represent, not just who they are.
Response is most effective when it is collective action with clear communication, shared planning, and practical support across teams.
Earlier awareness doesn’t prevent everything, but it allows teams to:
Understand emerging narratives
Prepare communications in advance
Brief staff and leadership
Support affected individuals with context
Adjust safety plans
Coordinate internally rather than reacting under pressure
Even modest lead time can make responses more organized and less reactive.
Doxxing isn’t random. It follows patterns, and understanding those patterns helps organizations recognize risk earlier and respond with clarity.